“Cryptography ” comes from the Greek word “krypto” meaning “secret ” or “hidden”. The art of writing secret message is called cryptography. It used to protect confidentiality, ensure integrity and guarantees authenticity and nonrepudiation .
Hashing – Crypto
Message Digest ( one way hash) Functions : Hash function calculates the unique fixed size ( 128/256 bits) string representation of any arbitrary block of information . The below message digest functions are widely used :
1. MD5
2. SHA
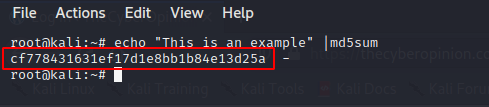
MD5 (Message Digest 5)
– MD5 takes a message of arbitrary length as the input and then outputs a 128 bit fingerprint .
–MD5 algorithm comes into use in a wide variety of cryptographic application and is useful for digital signature , file integrity checking and strong passwords.
– MD5 is not collision resistant and therefore the latest algorithms such as SHA-2 and SHA-3 is recommended.
SHA (Secure Hashing Algorithm )
The secure hashing algorithm is developed by NIST ,specified in Secure Hash Standard (SHS) and published as a federal information processing standard(FIPS PUB 180). It has three generation SHA-1, SHA-2 and SHA-3.
SHA1 is no longer approved for cryptographic operations.
SHA2 is a family of two similar has functions, with two different block sizes, namely SHA-256, which uses 32 bit words and SHA-512, which uses 64 -bit words.
SHA3
More here : https://cryptobook.nakov.com/asymmetric-key-ciphers/ecc-encryption-
https://developer.android.com/guide/topics/security/cryptography
java-crypto-lib-bouncy-castle/
android-crypto-libspongy-castle
Applications of Hash Functions:
Password Storage :
- Instead of storing password in clear, mostly all logon processes store the hash values of passwords in the file
- An intruder can only see the hashes of passwords, even if he accessed the password. He can neither logon using hash nor can he derive the password from hash value since hash function possesses the property of pre-image resistance.
Data Integrity Check
Data integrity check is a most common application of the hash functions. It is used to generate the checksums on data files. This application provides assurance to the user about correctness of the data.
The integrity check helps the user to detect any changes made to original file. It however, does not provide any assurance about originality. The attacker, instead of modifying file data, can change the entire file and compute all together new hash and send to the receiver. This integrity check application is useful only if the user is sure about the originality of file.