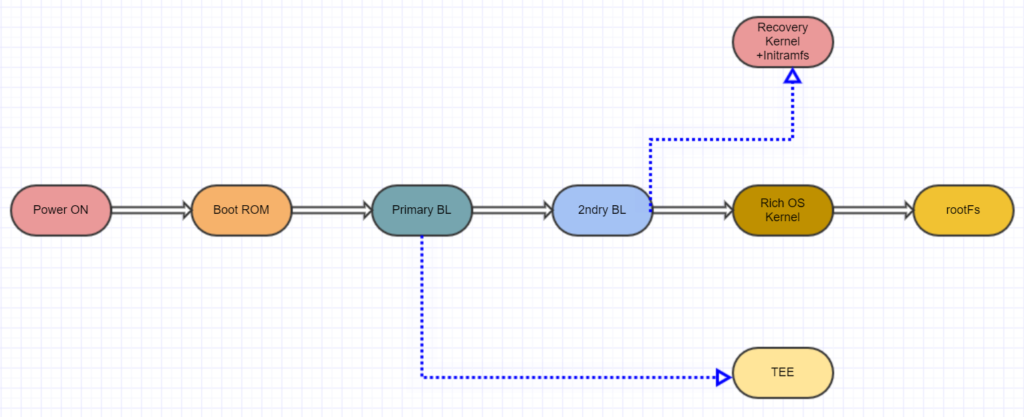
Secure boot assures that device boots using only software that is trusted and has not been tempered . The boot process consists of various components and the integrity of each succeeding component is verified according to the given reference and a chain of trust is established. This chain can be represented by the recurrence:
I0 = True;
Ii+1 = Ii ∧ Vi(Li+1) ; where Ii denotes the integrity of layer i and Vi is the corresponding verification function. The verification function performs cryptographic hash of the ith layer, and compares the result to the reference value.
Note: To be noted that without the integrity of the initial boot code ( represented by the I0 ) any further integrity verification becomes pointless. Thus, the initial boot code is protected by a tamper-evident hardware module.